We specialisE in offensive and defensive Cyber Security





who we work with
Our consultants have first-hand experience in securing Enterprise, Critical Infrastructure, Government, Defense and Regulated business sectors against current threats. By constantly investing in our team through industry leading training, tools and internal development.

The tech we use
We pride ourselves on our technical capabilities paired with a customer-focused approach, ensuring quality over quantity and providing high value services.






case studies
EVENTS AND LOGS are not monitored to detect attack

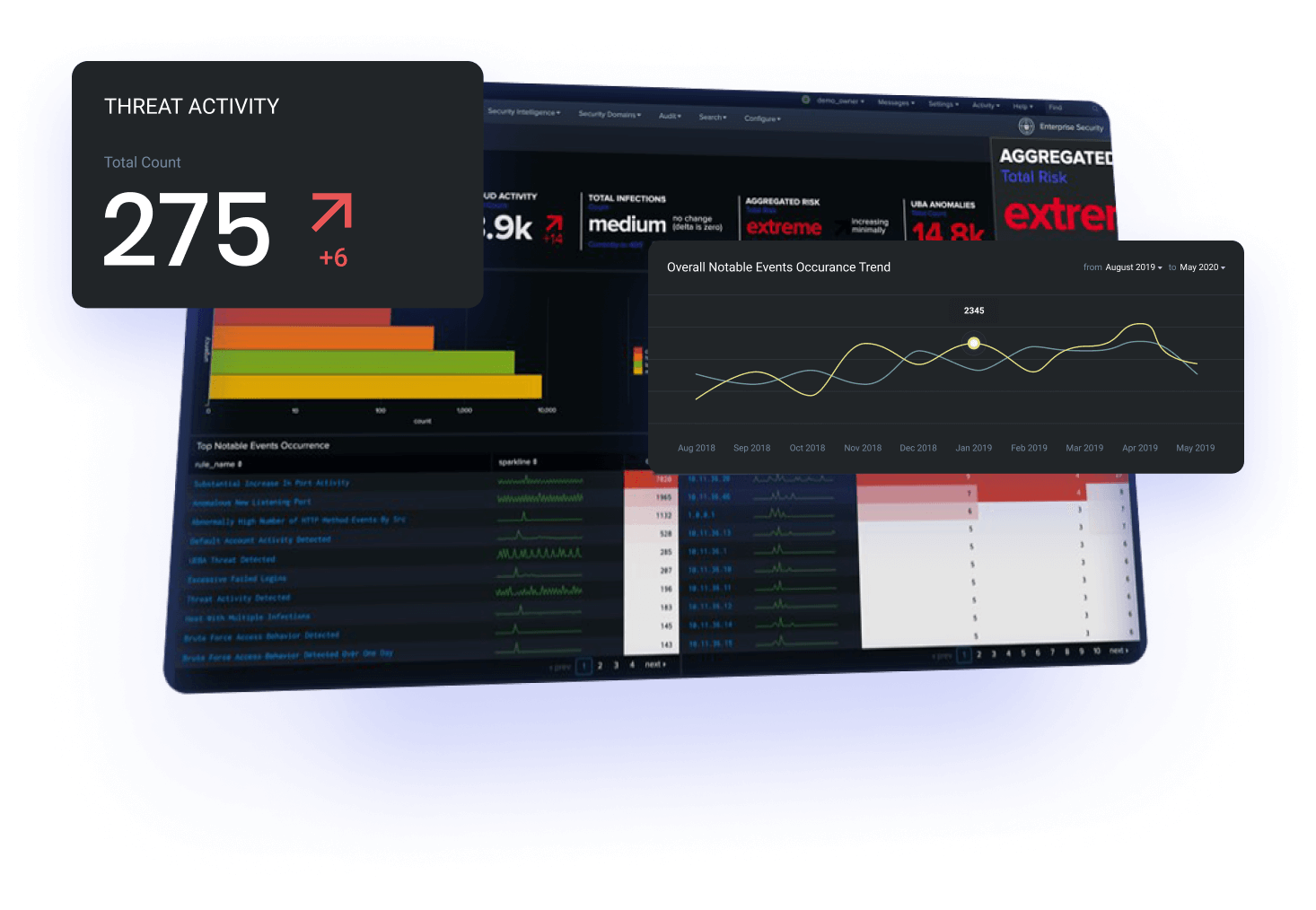
Alchemy identify critical assets and design a SIEM
Alchemy worked with key stakeholders to identify business critical assets, information and processes. Using this information a SIEM was designed and implemented to centralise logs and events while enabling the business to proactively correlate and identify threats within all tiers of their environment.

effective identification & Defence against attack
This gave the business granular visibility across their environment, enabling them to proactively identify and defend their business against advanced attacks.

Splunk was used to mature defensive capabilities
Splunk is still considered the industry standard SIEM product on the market, we have utilised the flexibility of this product across a wide range of customers to dramatically mature the defensive capabilities of our customers.

They UnderstooD emerging tecHnology and threats
AlchemySec is my go-to Cyber Security Consultancy, Every. Time. They are quick to answer an email for the “easy” questions, or give you the detail you need to convey an issue to a client. Having worked in both the Enterprise space, as well as the Small-to-Medium business, they understand what you are trying to achieve and knows how to get the job done. I can’t recommend them highly enough.



