Fast threat detection & remediation
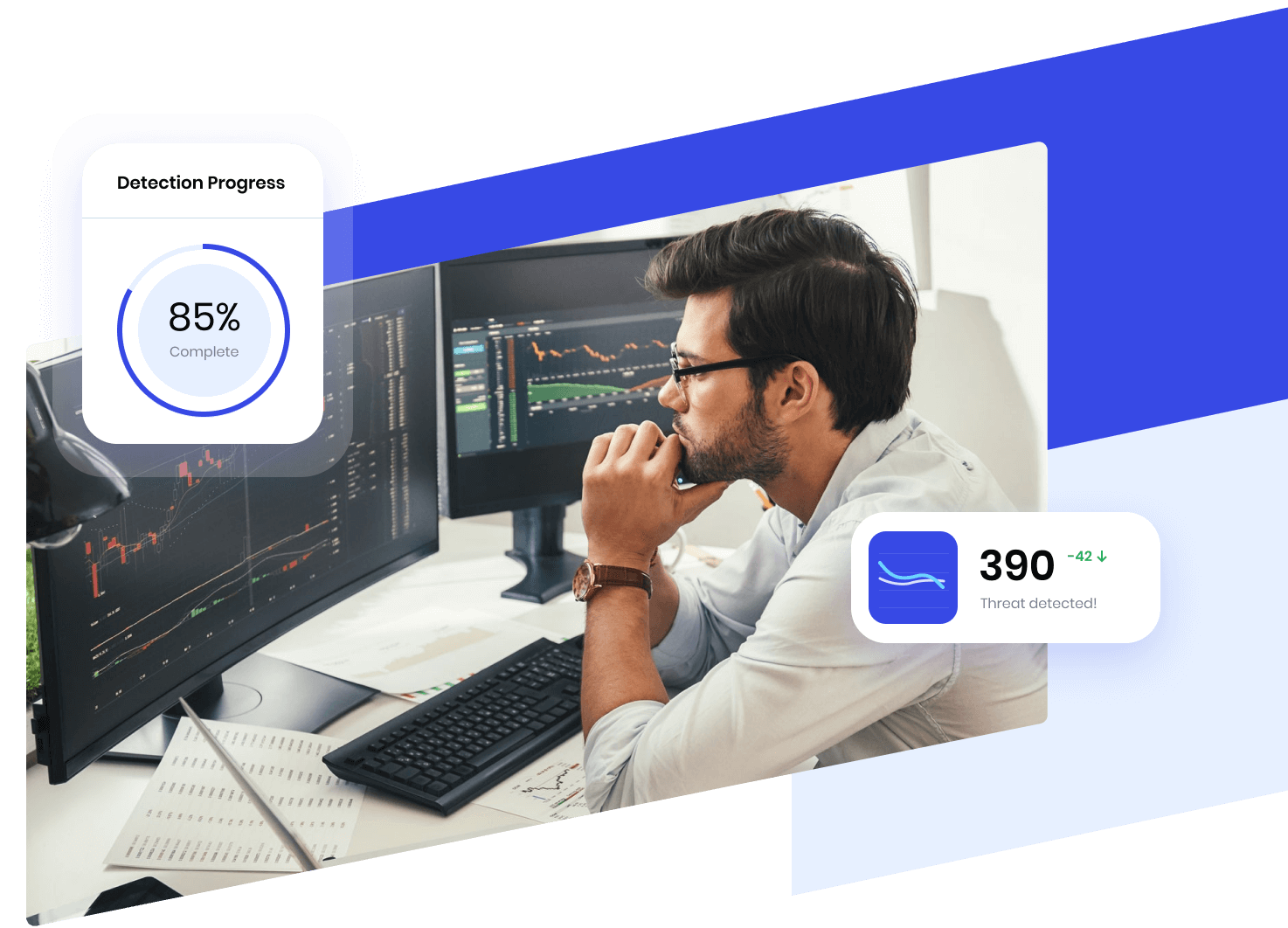
What happened, how it happened & How to resolve it
Our team will perform a comprehensive forensic and log analysis to identify what happened, how it happened and the best course of action to resolve the breach. We will work with your organisation and any incident response procedures that are in place to provide assistance (Annual IR retainer options available).
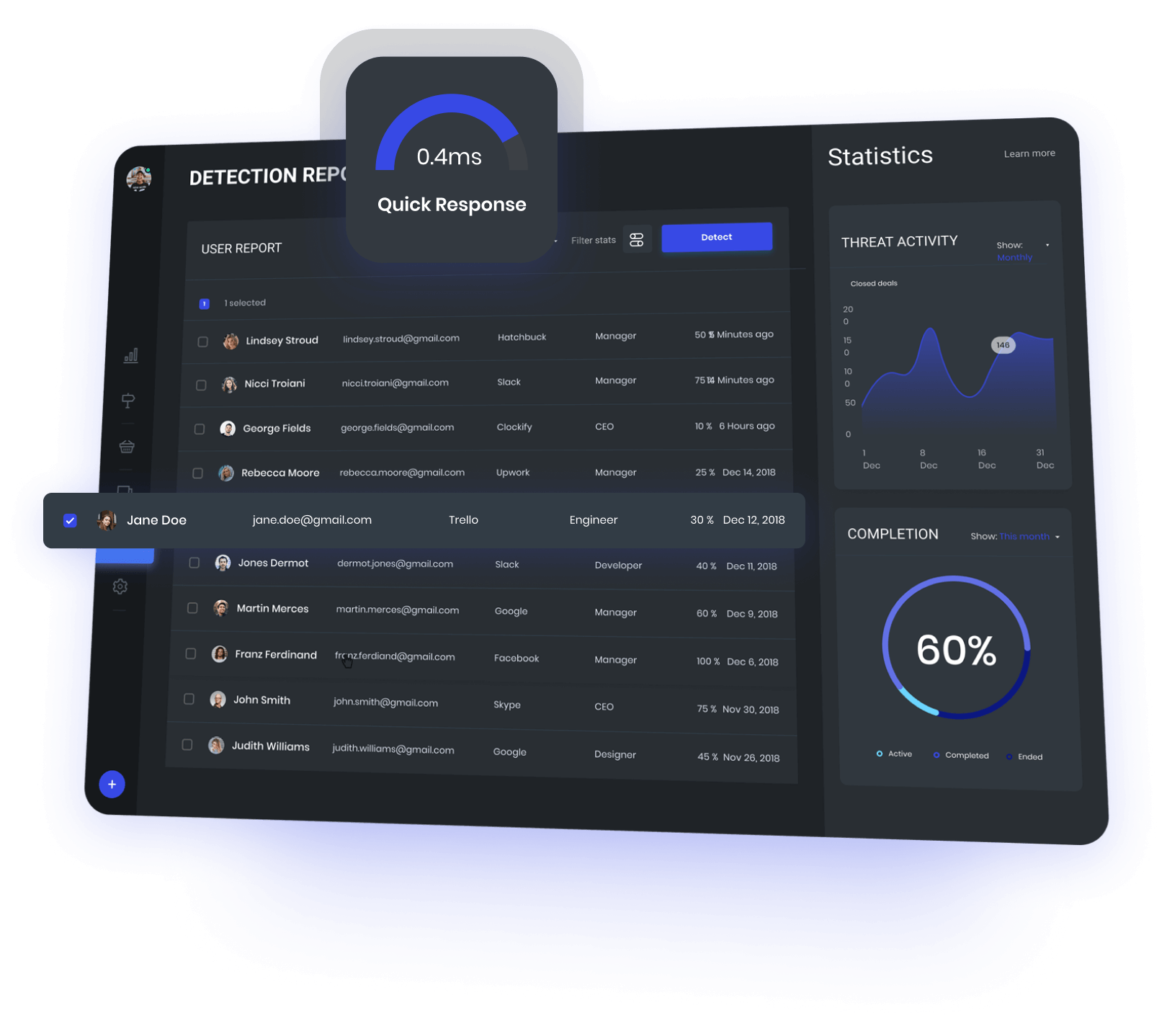
Forensic & Log Analysis
Our team will perform a comprehensive forensic and log analysis to identify what happened, and how it happened.
INCIDENT RESPONSE RETAINER
Enable your business to access the technical resources required to respond to a breach in an agreed timeframe.
TIMELINE based reports
All findings are documented in a timeline-based report, detailing all findings and recommended remediation actions.

We use industry-leading siem software to detect & Analyse threats
Our team has extensive experience with a wide array of industry-leading SIEM platforms and are ready to assist you with everything from a brand new implementation through to specific use case integrations.
WHAT IS A SIEM?
A SIEM (Security Information and Event Management) service centralises logs within an environment for both security monitoring & incident response purposes.
IMPLEMENTATION
We will design and implement an effective SIEM tailored to your business.
MATURING YOUR SIEM
We will identify key areas to mature the detection capabilities effectiveness of your SIEM.
case studies
EVENTS AND LOGS are not monitored to detect attack

Alchemy identify critical assets and design a SIEM
Alchemy worked with key stakeholders to identify business critical assets, information and processes. Using this information a SIEM was designed and implemented to centralise logs and events while enabling the business to proactively correlate and identify threats within all tiers of their environment.

effective identification & Defence against attack
This gave the business granular visibility across their environment, enabling them to proactively identify and defend their business against advanced attacks.

Splunk was used to mature defensive capabilities
Splunk is still considered the industry standard SIEM product on the market, we have utilised the flexibility of this product across a wide range of customers to dramatically mature the defensive capabilities of our customers.

They UnderstooD emerging tecHnology and threats
AlchemySec is my go-to Cyber Security Consultancy, Every. Time. They are quick to answer an email for the “easy” questions, or give you the detail you need to convey an issue to a client. Having worked in both the Enterprise space, as well as the Small-to-Medium business, they understand what you are trying to achieve and knows how to get the job done. I can’t recommend them highly enough.

Our Unique Process We Developed Over 10 years.
Alchemy Security Consulting Pty Ltd provides a broad range of security assessment services to assist our customers in identifying vulnerabilities and maturing their defensive capabilities.
scoping
The scope will define the objectives, constraints, scheduling and reporting requirements for the assessment.
assessment execution
We will execute the assessment in line with the agreed scope.
reporting
All findings will be documented in a risk prioritised report detailing all findings and recommended actions.
remediation testing
A retest of key findings is performed to validate that remediation actions by the customer have successfully mitigated identified vulnerabilities without introducing further vulnerabilities or risks.
List all the benefits
Further to that it also gives an opportunity for the business look at lessons learnt to mature their internal incident response procedures.
Our retainers are tailored to your requirements and allow you to maximise the return on investment by allowing you to utilise your retainer to consume other services through us such as penetration testing or architecture reviews.


