
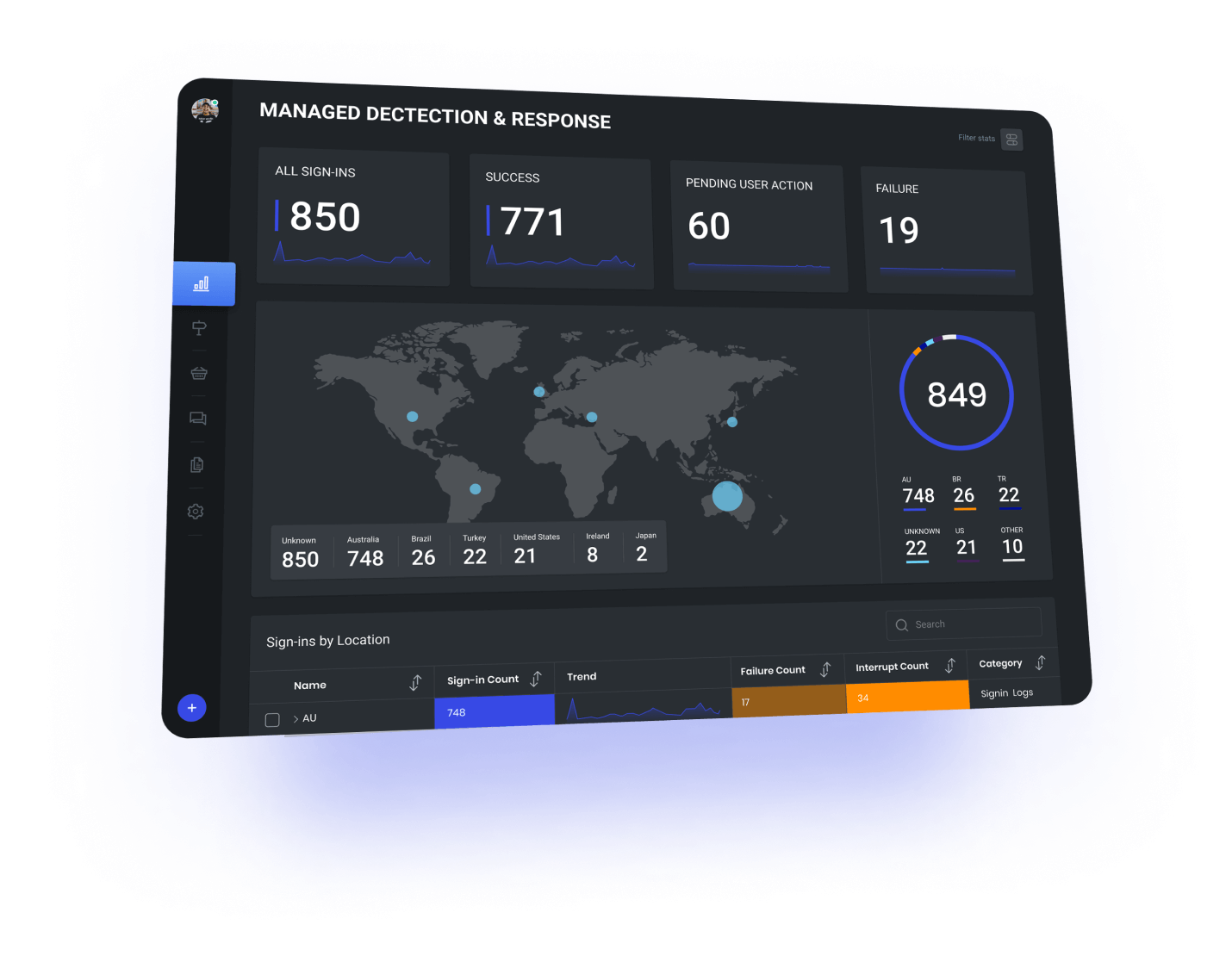
Our Managed Detection & Response service combines best of breed technology and expertise with skilled and experienced analysts to provide advanced detection and response capabilities. This combination allows us to reduce the impact of a breach or incident and, rapidly mature the defensive capabilities of our customers.
Best of breed technology combined with Alchemy's inhouse detection strategies detect and defend your environment against advanced and persistent threats.
Alchemy's skills and experience in both incident response and red teaming allows us to proactively hunt for threats within your environment. Proactively identifying threats that technology and product alone cannot.
Granular visibility, best of breed technology paired with skilled and experience security consultants rapdily matures your cyber security capabilities
Our MDR services are built on best of breed technology such as end-point detection and response (EDR) and security information and event management (SIEM). While these technologies in isolation are effective, our skilled and experienced consultants fill the gaps in detection techniques that technology in isolation cannot.

Managed Detection & Response Features
| Features | Foundation | Advanced |
|---|---|---|
| End-Point Vulnerability Management | ||
| End-Point Detction & Response | ||
| 24x7 Monitoring | ||
| All incidents reviewed and validated | ||
| Security Team respond to threats on your behalf | ||
| Regular consults and reporting | ||
| Incident Response assistance | 1 p/y | 2 p/y |
| Access to Azure Sentinel | ||
| User and Entity Baseline Analytics (UEBA) | ||
| Manual Threat Hunting to Identify Advanced Persistent Threats |
| Features | Foundation | Advanced |
|---|---|---|
| Dedicated security consultant | ||
| Reviews/Triages alerts and incidents | ||
| SIEM Support | ||
| Scheduled consultations with security consultant | Quarterly | Monthly |
| Assistance with management and executive reporting | ||
| General security consulting to assist in broader security decisions | ||
| Communicates impact and findings of threat hunting |
| Features | Foundation | Advanced |
|---|---|---|
| Advanced persistent threat TTP detections | ||
| Zero-Day vulnerability detection | ||
| User and entity baseline analytics (UEBA) | ||
| Threat intelligence | ||
| Manual Threat Hunting to Identify Advanced Persistent Threats (APT) |
| Features | Foundation | Advanced |
|---|---|---|
| Security team respond, validate and triage alerts and incidents | ||
| Security team will perform actions on infected hosts to isolate threats | ||
| Security team will perform incident response to assist in managing an incident |
| Features | Foundation | Advanced |
|---|---|---|
| Alert and incident reports with tailored remediation and mitigation actions | ||
| Onboarding red team validation test | ||
| Onboarding threat hunting report | ||
| Threat analytics reporting | ||
| Monthly Vulnerability Report | ||
| Customer specific reporting | ||
| Monthly threat hunting reports |
| Features | Foundation | Advanced |
|---|---|---|
| Self service alerting and reporting | ||
| Implementation, setup and configuration assistance (SIEM) | ||
| Self service log management, searching and reporting capability (SIEM) |
Our Managed Detection and Response service stays on the very cutting edge of both detection and response capabilities.
Alchemy Sec's Managed Detection and Response prepares you to both identify and react to a breach by rapidly maturing your defensive capabilities and incident response processes.
Threats are proactively identified by advanced detection techniques paired with best of breed technology and experienced security consultants.
Once a threat has been identified, containment strategies are implemented to limit further impact and lateral movement.
Through investigation and hunting strategies, infections and persistence mechanisms are removed through both remediation and restoration activities.
All impacted end-points, accounts and services will have numerous recovery actions performed to ensure that vulnerabilities exploite by the threat actor have been appropriately remediated.
The final phase allows us to review the incident as a whole, identifying what was done well and what could have been done better to further improve future incident response capabilities.
AlchemySec's MDR capability is built upon experience gained from years of incident response and red team engagements that allow us to rapidly mature our customers incident response capabilities, mitigate attacks and proactively identify breaches.

Alchemy worked with key stakeholders to identify business critical assets, information and processes. Using this information a SIEM was designed and implemented to centralise logs and events while enabling the business to proactively correlate and identify threats within all tiers of their environment.

This gave the business granular visibility across their environment, enabling them to proactively identify and defend their business against advanced attacks.

AlchemySec is my go-to Cyber Security Consultancy, Every. Time. They are quick to answer an email for the “easy” questions, or give you the detail you need to convey an issue to a client. Having worked in both the Enterprise space, as well as the Small-to-Medium business, they understand what you are trying to achieve and knows how to get the job done. I can’t recommend them highly enough.
