Part of performing an effective and successful penetration test requires gathering as much information about the target as possible. The more information you have on your target, the more likely you are to discover an exploitable service or land a successful phish.
For example, through OSINT you may discover that the target is openly advertising a job position, and invites applicants to send a resume through to HR. You craft a document using template injection to pull a C2 beacon from one of your C2 domains and can achieve a foothold on the internal domain by mimicking a job applicant.
Without effective recon, it is likely that this opportunity may be missed resulting in an extended period attempting to gain an internal foothold.
So how do you go about effective OSINT/recon?
While breach data may not always contain information on your target, or even recent or up-to-date passwords, it can provide valuable information.
For example, it can give an idea of if users practice sensible account hygiene and register for non-work websites using work email addresses. It can also provide an indication of how users structure their passwords. While “Mary1987” may not be the most recent password, it indicates password format in the form of “NameYear” may be suitable for password spraying.
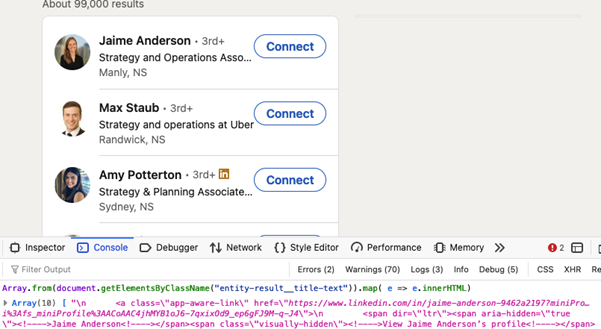
Social media is a good place to identify employees at your target. LinkedIn generally provides a solid list of employee names, along with job titles that can help you land a juicy phish.
Creating a list can be done using JavaScript to print employee names to console, or you can use the BurpSuite plug-in GatherContacts.
Social media can also be useful for determining what relationships a business might have with other companies in the same industry that could be exploited, or what technology might be in use that may need to be avoided when you gain an internal foothold.
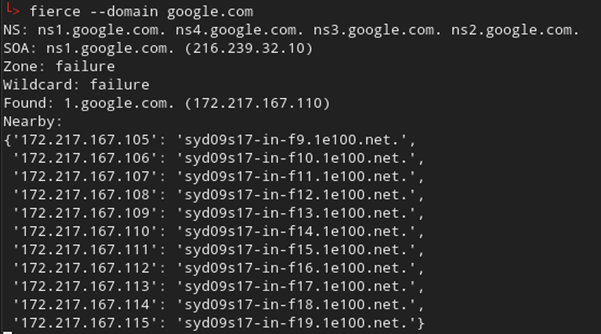
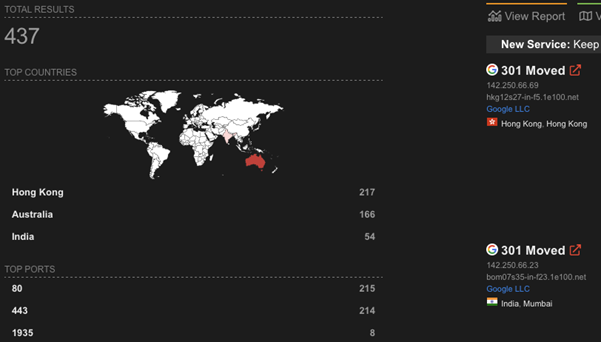
DNS records can also reveal a large amount of information regarding potential targets and remote entry points such as VPN or RDP gateways. In addition, with a lot of organisations moving to cloud platforms it can also help identify issues such as subdomain takeovers (they still very much exist in 2021!)
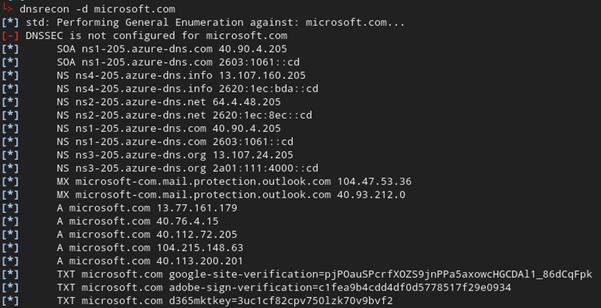
One thing you should be wary of with DNS is that it can be noisy if you start querying the organisations DNS servers directly, so depending on how stealthy you need to be, this may need to be done via historical DNS records and/or certificate transparency lookups.
A number of tools exist that can automate some of this reconnaissance. During a time-limited penetration test these can be quite valuable, as they allow you to work on other tasks while the information is gathered.