The Conti group have been featured across many news outlets lately both inside and outside the cyber security community. It is well known that this specific threat actor is mainly operated from within Russia, and with the recent events within Russia and Ukraine we thought it would be a good idea to do a recap on this treat actor group. In this post we’ll aim to cover some of the tooling utilized by the threat actor as well as their involvement within the recent Russia and Ukraine conflict.
We encounter this group on a regular basis through our Managed Detection and Response service, and our incident response engagements. This threat actor behaves much like a business with a broad range of internal resources and departments to leverage as part of their ransomware service.
While there are a broad range of publicly available Indicators Of Compromise (IOCs) for this threat actor, we will cover some of the tooling we have seen them used recently which will typically fly under the radar of common security controls.
As a group Conti makes their money through their ransomware service, once they have gained access to an environment with elevated privileges, they will rapidly look to destroy backups before deploying their ransomware to as many machines as possible. Besides operating more as a business rather than a typical hacker group, they also attempt to ensure their attacks do not impact critical infrastructure. While critical infrastructure typically includes power grids and utilities, Conti are mainly referring to health care infrastructure such as hospitals.
However, with the recent conflict in Ukraine Conti have thrown their support behind Russia by publicly stating they will proactively target the critical infrastructure of countries that get involved with the conflict through cyber-attacks against Russia.
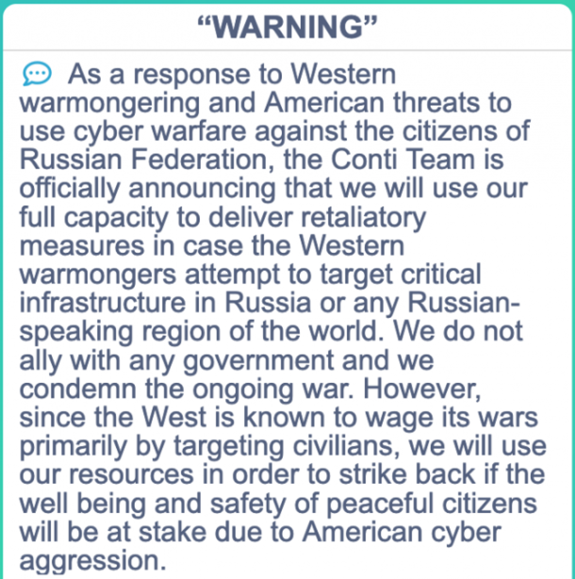
With this specific threat actor being so successful against targets around the world, especially in Australia, it is important to understand the TTPs associated with this threat actor to better defend against them. This is especially important if your business or environment is considered critical infrastructure.
It has been long suspected that certain crime groups operating out of Russia have had various levels of support from their government. While there isn’t a lot of publicly available concrete evidence to suggest this is the case, documents have been leaked by a Ukrainian within the Conti group that suggests Conti have ties to the Russian Fedaral Security Service.
The below screenshot is from a Conti Jabber conversation where they discuss having gained access to some information detailing correspondence between the victim and the journalism organisation Bellingcat.
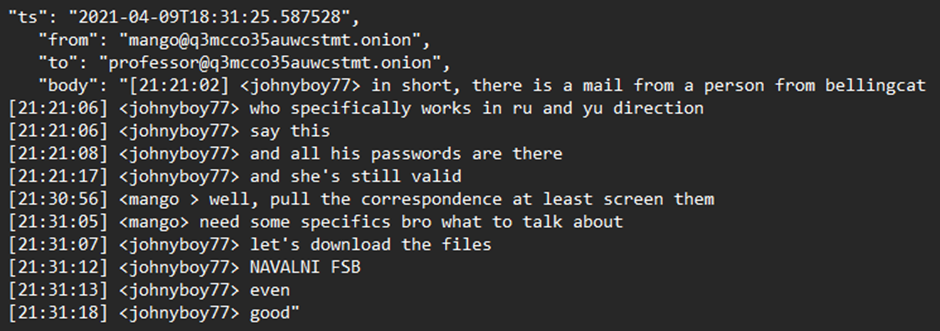
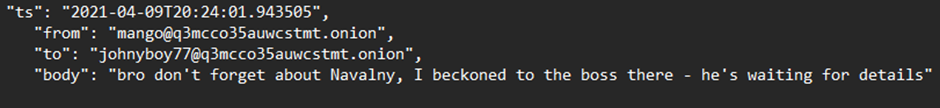
Of particular interest is the mention of Navalny and FSB within the same chat log, this does seem to suggest that to an extent Conti has a connection or contact at the FSB, how far this relationship goes is yet to be seen.
The Conti group utilize a broadrange of Tools, Techniques and Processes. We are going to take this opportunity to briefly recap on some of the most common TTPs utilized by the group. As part of this we are also going to touch one some ‘greyware’, legitimate applications utilized by the crew to achieve persistence without raising the suspension of security controls.
Trickbot has been around since 2016, originally only observed being utilized by APT group Wizard Spider. This piece of malware is a feature rich application that provides the threat actor with a huge range of capabilities to facilitate persistence, lateral movement, and enumeration activities.
Emotet has been operating since 2014 and was typically classified as a banking trojan and spread through broad phishing campaigns. This malware is typically used by groups as a deployment mechanism. Once the malware has successfully executed on an endpoint, the operator can distribute other malware such as Trickbot and Cobalt Strike.
Cobalt Strike is an Adversary Simulation and Red Team Operations tool built for security teams and penetration testers to easily simulate an advanced threat. Think of this tool as a commercial command and control application. Unfortunately, even though Cobalt Strike perform diligent background checks on all of their customers, the application has been leaked multiple times and is now a staple tool for the Conti group.
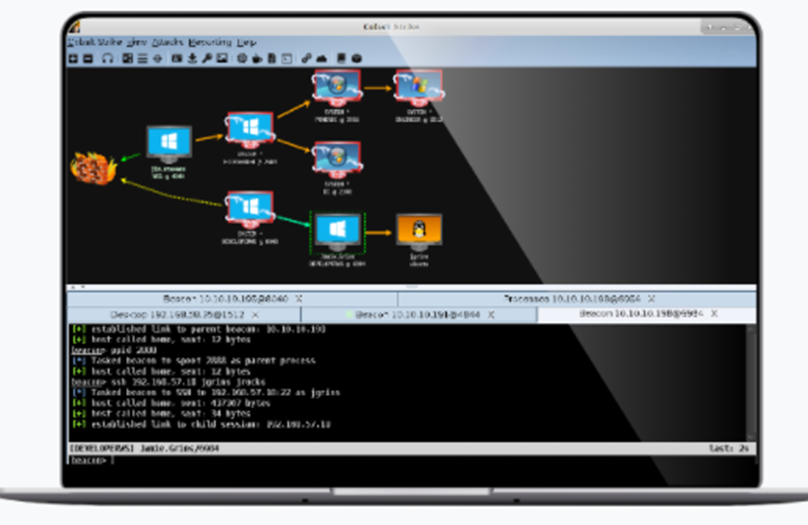
In recent attacks we have noticed a significant shift in Conti’s tradecraft where they have adopted the use of legitimate tooling for both persistence and command and control. This includes utilizing applications that have legitimate real-world purposes such as applications commonly utilized by developers and Managed Service Providers (MSPs).
These applications will typically go unnoticed by most security controls purely because they are a legitimate application used by a huge number of legitimate businesses globally. While controls such as Endpoint Detection and Response (EDRs) will likely generate an alert that this is a potential risk, they typically do not prevent the application from executing.
Atera is a remote management tool developed for MSPs to allow them to easily support their customers through the remote management capabilities of the Atera application. While the technique of using remote access tools for persistence or command and control is not new, the licensing model of Atera resonates with Conti’s processes like no other. Typically, once the group has administrative access within an environment they will register for an Atera instance utilizing a public email address aligned to the internal domain name of the compromised environment. While it is not clear whether the group utilises a free trial for their entire engagement, Atera is licensed per consultant. This means they can essentially deploy the tool across an entire environment without running into any ‘per machine’ licensing issues.
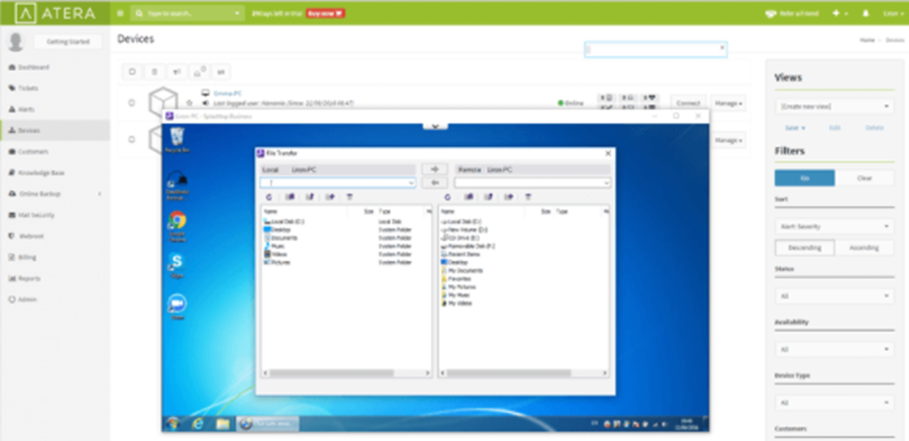
Ngrok is a tool that once installed on a machine can be configured to expose a service on the host to the internet. This is done by tunneling the network traffic over HTTPS to the Ngrok service, where Ngrok then provide a url and port that the user can hit to access the desired service.
Conti typically utilize this service to expose remote access protocols such as Remote Desktop Protocol (RDP). This allows them to gain a RDP session on a host that typically is not directly exposed to the internet and makes it easier for them to perform lateral movement.
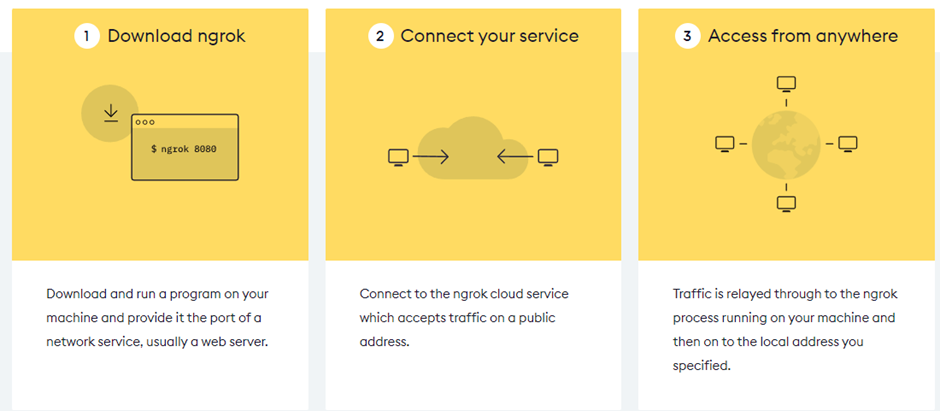
CrossTec is a tool that is very similar to Atera in that it is typically utilized by an MSP to provide remote support to their customers. CrossTec is not as feature rich as Atera however it does provide the same level of remote access and persistence to the threat actor.
Conti are opportunistic, with most of their successful attacks beginning with a phishing email, password-based attack or exploitation of a 0-Day vulnerability such as LOG4j. If an environment looks to be too mature, they will simply move on to next target to increase the likelihood of a successful attack.
Mitigating most threat actors, including Conti can be achieved using fairly common security controls.
https://www.cyber.gov.au/acsc/view-all-content/advisories/ransomware-profile-conti
https://krebsonsecurity.com/2022/03/conti-ransomware-group-diaries-part-i-evasion/