Modern environments are in a constant state of flux; new systems are being commissioned, and old systems decommissioned, to meet new requirements and increase efficiency in all sectors. Managing those changes takes strategy and labour, and every change has an overhead in both of those resources.
What do you do when your users want new software, or to be able to update their apps without waiting for the next patch window?

It’s the perfect solution, your users can now:
And all this without taking up IT resources for changes that may only affect a single endpoint. Sure, everyone needs email but how many users need software for CAD, tax reconciliation, or even software development?
Many businesses decide that the cost to the business, and frustration of users, is too high and provide admin access to users over their own machine. Some may even give functional groups admin to all the endpoints in their team via security groups.

A significant downside of this strategy is loss of both control and visibility over endpoints. You don’t have to patch applications now, but are your users doing it? Maybe they’ve installed chrome and they’re keeping it up to date, or maybe they’re using a portable Firefox on a USB they bring from home – the same one they use to clean up viruses on their parents’ home PC.
If you’re letting users install their own software, answering these questions is going to be hard:
Let’s have a look at ACSC’s Essential Eight Controls to mitigate exploitation. These are the Australian Government’s recommendation for the 8 most important controls to protect your business.
Let’s see how they align with allowing:
At this point, allowing Local Administrator access has weakened or invalidated the most effective controls we have.
OK, so we’ll get EDR to detect malicious activity. At least this way attackers can’t use tools to exploit other machines.
Oh, yeah that. We can’t stop the tools from running because we can’t get visibility and execution control within a virtual machine. Ok, we’ll get a vulnerability scanner to detect exploitable vulnerabilities – even if we can’t control the applications, we can scan for vulnerable installs to fix.
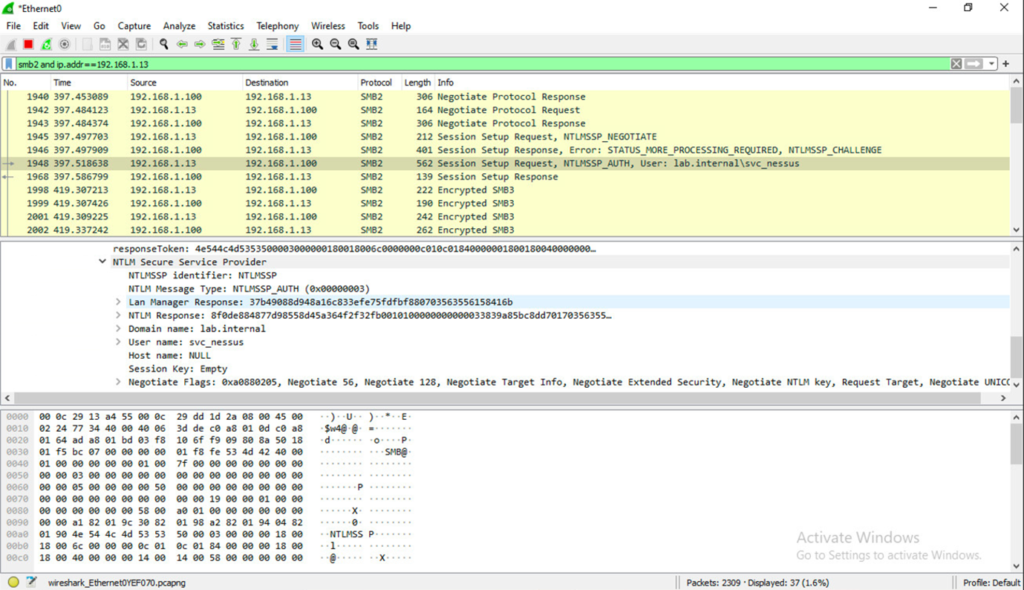
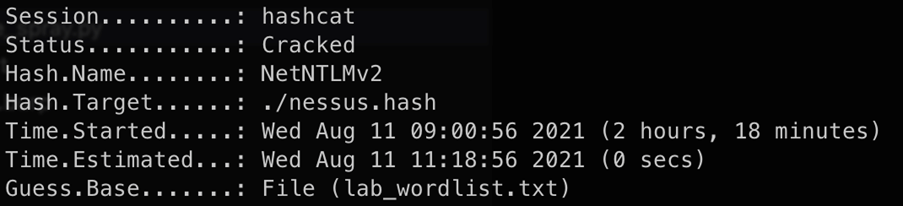
Oh, we made the scanner service a domain admin to have one account to scan all our machine. Now we need privileged account management anyway to detect and prevent the scanner account being used outside scanning schedules.
The basic answer here is – administrative privilege is a risk. One of the best ways to prevent exploitation is to limit its usage for administrators, any expansion pollutes your environment.
Giving users administrative access is giving away your control, and it’s hard to get that back.