Advanced persistent threats come in many forms ranging from your crime groups, activists all the way through to your state sponsored groups. While some of these threat actors such as crime groups are seen on a regular (if not daily..) basis, state sponsored attacks are less common and more sophisticated. While most state sponsored groups are engaged in similar activity, there is one group specifically that bridges the gap between your typical state sponsored and crime group.
Introducing, Hidden Cobra AKA Lazarus Group, the North Korean state sponsored threat actor.
Generally, state sponsored APT groups have a similar focus on espionage activities, typically targeting government, critical infrastructure and defence industries. Hidden Cobra however are known for engaging in a broad range of crime-based activity from ransomware all the way through to bank and cryptocurrency exchange heists since roughly 2009. We have listed a few of the better-known attacks Hidden Cobra have conducted below.
We are going to explore the more recent activity of the AppleJeus campaigns to highlight some of the interesting Tools, Techniques and Processes utilised by Hidden Cobra.
This specific malware is solely attributed to Hidden Cobra and to date, no other threat actors have been documented using this malware. It has been used in various campaigns to specifically target users of Cryptocurrency trading applications as well as Cryptocurrency exchanges themselves. This malware has been actively deployed and matured since its inception in 2018 across multiple campaigns as documented below from US-CERT.
AppleJeus is distributed via websites that impersonate a legitimate application or service. Typically these services or applications are related to cryptocurrency, however Hidden Cobra have also been seen impersonating IT administrative tools.
The attacker would take the legitimate application and repackage it to include their own malicious code. In some instances the application itself was injected with the malicious code, however in some instances the attacker would simply package a malicious binary along with the application using tools such as Advanced Installer and AutoIT.
The threat actor would then host the repackaged/modified application on their impersonated website, before referring users to the malicious website via posts on numerous cryptocurrency forums.
Included below are just a few examples of websites and applications that have been impersonated and used by Hidden Cobra as part of their ongoing AppleJeus campaigns to date.
This AppleJeus campaign was identified in August 2018 and was distributed via a modified and backdoored version of 'Q.T. Bitcoin Trader'. The malware itself was hosted on celasllc[.]com with both Windows and MacOS versions available for download.
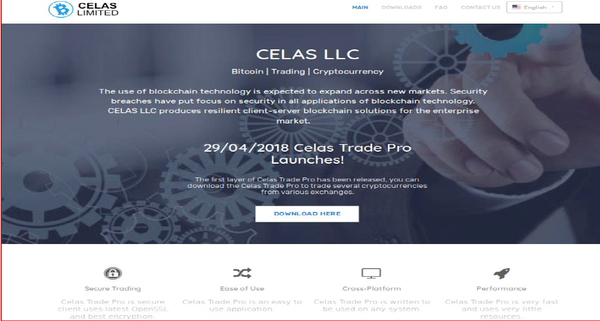
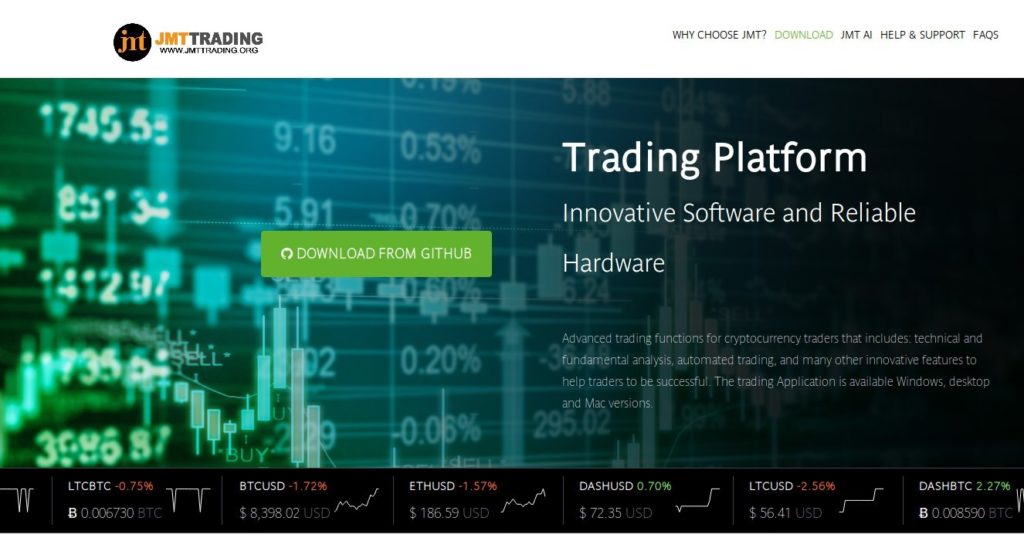
The JMTTrading AppleJeus campaign was identified in 2019, distributed again with a modified version of 'Q.T. Bitcoin Trader'. The malware itself was hosted on GitHub, with both prepackage and 'open-source' versions available for Windows and MacOS.
Union Crypto was another fake cryptocurrency trading application that was created solely to distribute the AppleJeus malware in 2019.

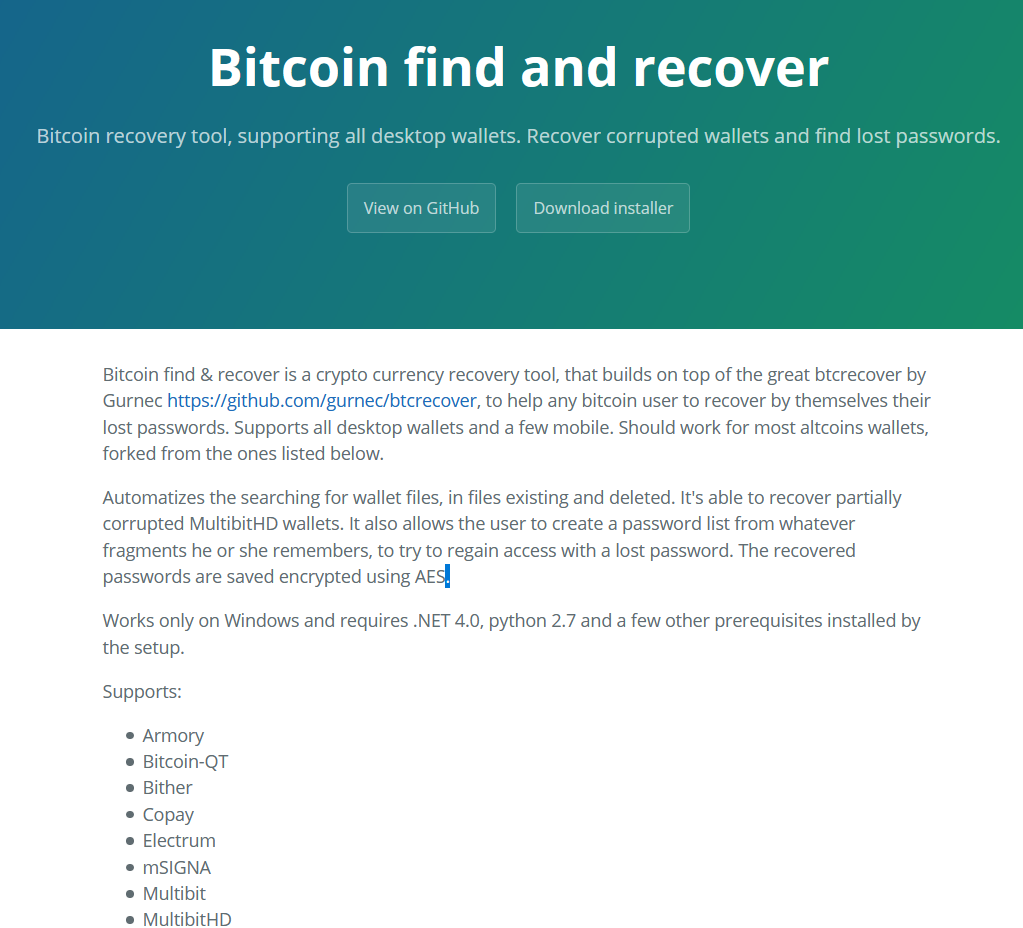
Bitcoin Find and Recover is a legitimate opensource bitcoin password and seed recovery tool. This legitimate tool was utilised to spread AppleJeus via a fake web page. The application itself was hosted prepackaged on the btcfindrecover[.]pw web server with a link back to the actual GitHub repository.
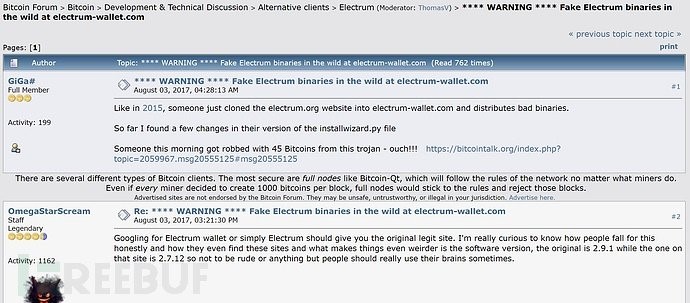
Electrum Wallet is a legitimate opensource bitcoin wallet application. The threat actor bundled their malicious code with the application using packaging software such as 'Advanced Installer'. Users were directed to download the backdoored application through forum posts.
AppleJeus malware has a particular focus on cryptocurrency, and it is distributed it in such a way to infect targets through both direct and indirect methods. By simply hosting their malware on their legitimate looking websites and referring target users or organisations to download and utilise the tool, they can compromise both corporate environments and individuals.
The malware itself will proactively and re-actively search for crypto currency wallets, usernames and passwords on the target machine before exfiltrating this data to command-and-control infrastructure via https post requests.
While specifically targeting cryptocurrency and banking sectors is not a characteristic unique to Hidden Cobra, it is a unique characteristic for a state sponsored threat actor. While state sponsored attacks are rarer in comparison to crime groups, Hidden Cobra are an example of how even the simplest looking attacks should be taken seriously. The AppleJeus malware itself is not advanced by any means, however as the target audience is broad, these campaigns manage to compromise both individuals and businesses across a vast range of verticals.
The graphs below show the geographical spread of infection based on command-and-control traffic to domains that were hijacked during a recent incident response engagement.
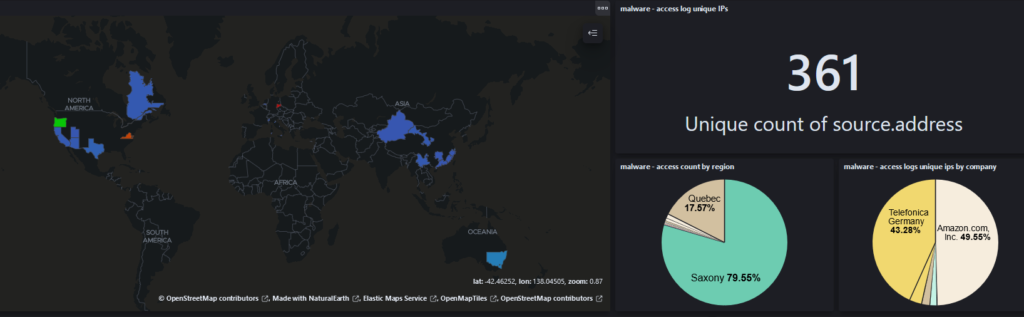
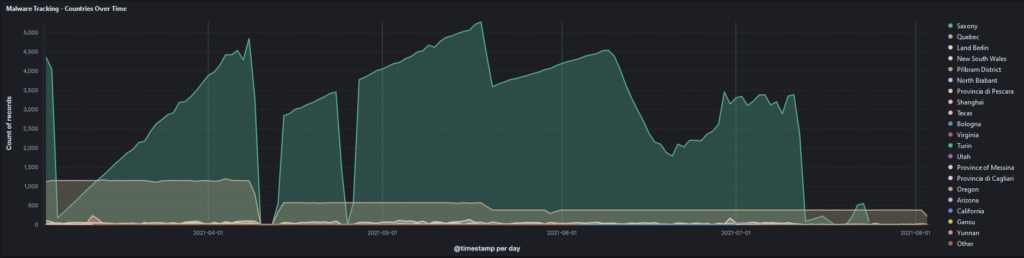
The TTPs employed by Hidden Cobra are not advanced; technology such as end-point detection response and application whitelisting are extremely effective at detecting and mitigating the TTPs associated with this threat actor. As an individual, secure practices such as hash-based validation are also highly effective practices to ensure that the file you are downloading is legitimate. Most developers will provide a list of hashes (Such as MD5, SHA256 etc..) that can be used to verify that the hash of the file you downloaded matches the hash supplied by the developer.
And finally, ensure that you always download applications from a trusted source.